
The Anubis ransomware-as-a-service (RaaS) operation has added to its file-encryptimg malware a wiper module that destroys focused information, making restoration not possible even when the ransom is paid.
Anubis (to not be confused with the same-name Android malware with a ransomware module) is a comparatively new RaaS first noticed in December 2024 however grew to become extra lively originally of the yr.
On February 23, the operators introduced an associates program on the RAMP discussion board.
A report from KELA on the time defined that Anubis supplied ransomware associates an 80% share of their proceeds. Information extortion associates have been supplied a 60%, and preliminary entry brokers a 50% reduce.
At the moment, Anubis’ extortion web page on the darkish net lists solely eight victims, indicating that it might improve the assault quantity as soon as confidence within the technical side is strengthened.
On that entrance, a Pattern Micro report printed yesterday incorporates proof that the operators of Anubis are actively engaged on including new options, an uncommon one being a file-wiping operate.
The researchers discovered the wiper within the newest Anubis samples they dissected, and imagine the characteristic was launched to extend the strain on the sufferer to pay faster as an alternative of stalling negotiations or ignoring them altogether.
“What additional units Anubis aside from different RaaS and lends an edge to its operations is its use of a file wiping characteristic, designed to sabotage restoration efforts even after encryption,” explains Pattern Micro.
“This harmful tendency provides strain on victims and raises the stakes of an already damaging assault.”
The harmful conduct is activated utilizing the command-line parameter ‘/WIPEMODE,’ which requires key-based authentication to concern.
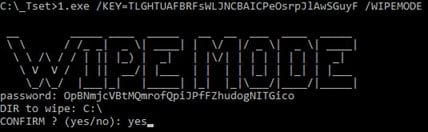
Supply: Pattern Micro
When activated, the wiper erases all file contents, lowering their sizes to 0 KB whereas retaining the filenames and construction intact.
The sufferer will nonetheless see all information within the anticipated directories, however their contents can be irreversibly destroyed, making restoration not possible.
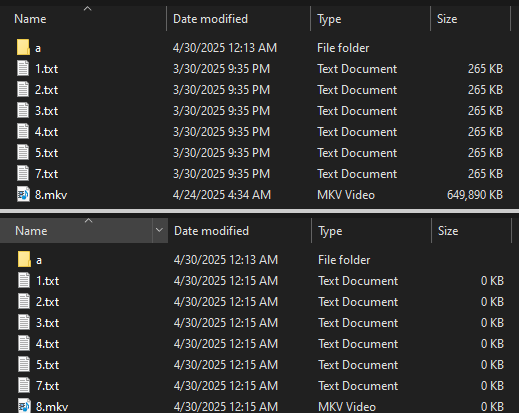
Supply: Pattern Micro
Pattern Micro’s evaluation reveals that Anubis helps a number of instructions at launch, together with for privilege elevation, listing exclusion, and goal paths for encryption.
Necessary system and program directories are excluded by default to keep away from rendering the system fully unusable.
The ransomware removes Quantity Shadow Copies and terminates processes and companies that would intrude with the encryption course of.
The encryption system makes use of ECIES (Elliptic Curve Built-in Encryption Scheme), and the researchers famous implementation similarities to EvilByte and Prince ransomware.
The encrypted information are appended the ‘.anubis’ extension, an HTML ransom be aware is dropped on impacted directories, and the malware additionally performs an try (failed) to alter the desktop wallpaper.
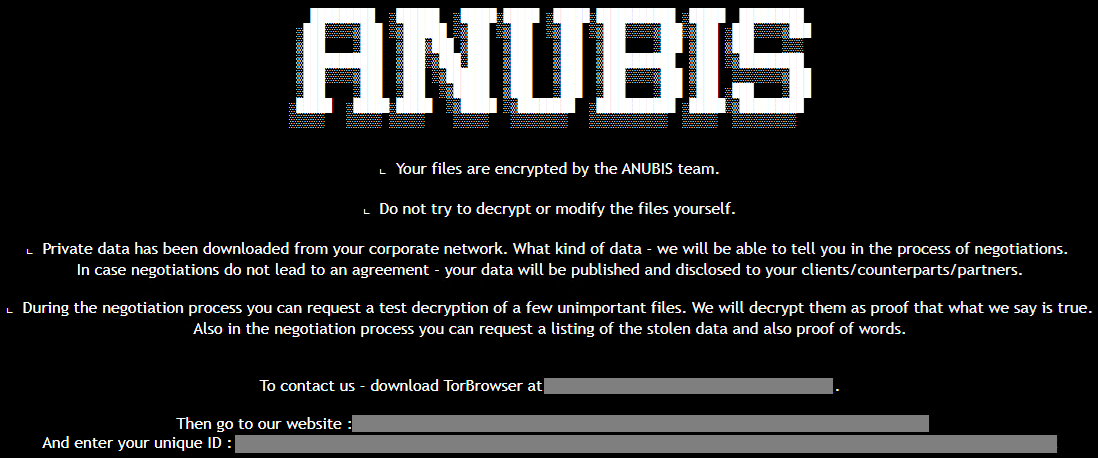
Supply: Pattern Micro
Pattern Micro noticed that Anubis assaults start with phishing emails that carry malicious hyperlinks or attachments.
The whole record of the symptoms of compromise (IoCs) related to Anubis assaults is out there right here.

Patching used to imply complicated scripts, lengthy hours, and limitless hearth drills. Not anymore.
On this new information, Tines breaks down how trendy IT orgs are leveling up with automation. Patch sooner, scale back overhead, and deal with strategic work — no complicated scripts required.

